The move to the cloud is becoming more popular for businesses and individuals. This is undoubtedly fueled by cloud-based technology’s ability to make communications, corporate infrastructure and productivity planning easier and more cost-effective.
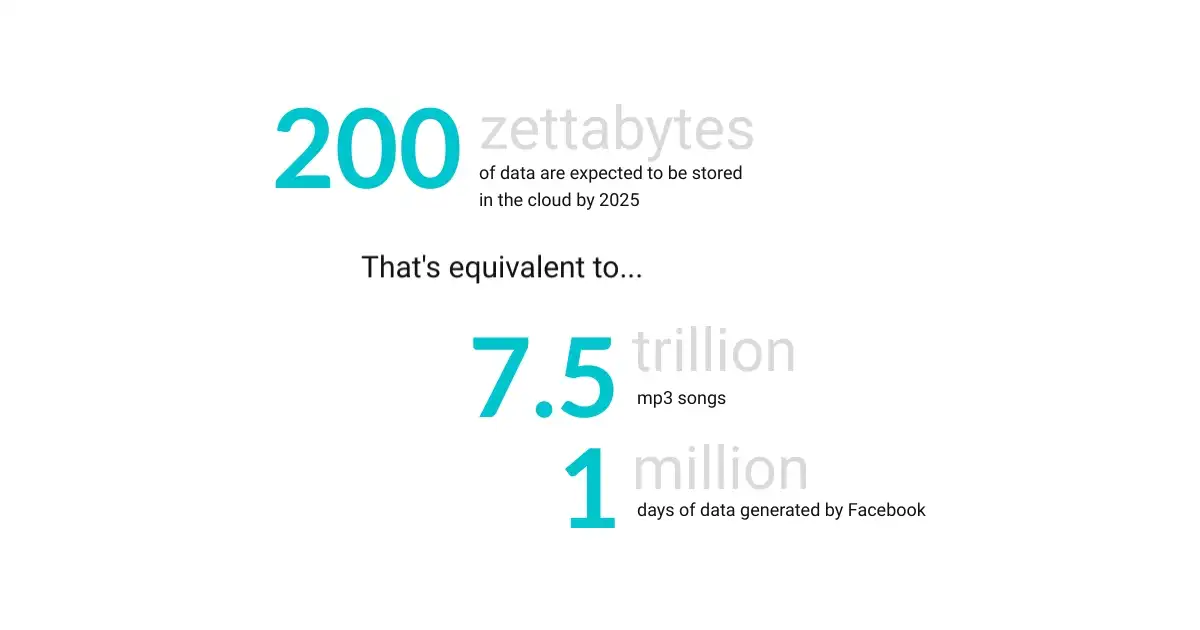
Our reliance on cloud systems and services is increasing so rapidly that by 2025, it’s estimated the cloud will be home to 200 Zettabytes of data.
To put that into a relatable context, that’s enough to store 7.5 trillion mp3 songs or 1 million days’ worth of data generated by Facebook.
But with this shift in technology comes the need for businesses to increase their understanding of managing and protecting their cloud environment.
Why Use Azure Cloud Security Best Practices?
While choosing a security-rich platform, such as MS Azure, as your cloud-based business solution is an excellent starting point, it’s often not enough.
Cloud-driven organizations with seemingly unlimited resources, such as Marriott International and LinkedIn, aren’t immune to security breaches in their cloud environments.
Top-notch security in any Azure environment requires following best practices throughout your projects’ deployment and operational phases. This is essential to prevent disastrous security breaches, ensure compliance with all stakeholders and regulatory bodies, and protect sensitive data.
Security in Azure Cloud Needs Assessment From All Angles
A cloud environment often comprises multiple workflows, deployment origins, network access points, third-party integrations and other operating system demands. Each parameter and function within a landscape needs to be evaluated for vulnerabilities during any Azure security assessment.
For instance, migrating from a native, on-premise solution to a cloud environment may introduce the need for increased security measures in previously secured endpoints. Examples can include CCTV equipment, communication systems, and internal devices.
Your system’s deployment processes must be considered for security as well. The architecture and framework of a system impact its security. How data moves from one workflow to another, encryption capabilities and network segmentation structures all play a vital role when creating a healthy security protocol for Azure landscapes.
[sc name=”more_posts”]
Learn more about Azure PaaS security on our blog: |
[/sc]
It’s easy to see that securing your Azure landscape requires a complex plan; your organization must take an all-encompassing approach when implementing a security plan. To make this process easier to manage, try to break it down into multiple parts or a checklist.
Azure Security Best Practices Checklist
When evaluating your current Azure security practices or developing one for a new landscape, be sure the development team can answer the following questions:
- What security measures are in place addressing your tracing deployment practices?
- What tools and processes keep operational procedures safe?
- What security techniques have been employed to monitor data access and usage?
- Are any third-party tools in use that are not up to date with Azure’s security requirements?
- What data encryption tools are in place?
- What security training do our users and stakeholders require?
Azure DevOps Security Best Practices
Zero Trust Based Access Control
Azure administrators should adopt a zero trust approach to their identity and access management protocols. Zero trust based access control eliminates weak points in networks where user access rights are based on the user’s identity. This helps prevent threat actors from gaining access to your network while ensuring your approved users can access data based on their assigned roles and responsibilities.
Multiple factor authentication (MFA) is an example of a commonly used zero-trust protocol.
Azure landscapes provide role-based access controls (RBAC) to quickly adopt a zero trust approach for managing privileged access to resources and services in the platform. RBAC allows you to define roles and assign users to those roles based on their responsibilities.
Data Encryption
Data protection measures are critical to the security of your Azure landscape. This includes passwords, operational data, personal information, customer and client records, proprietary information and more. Data encryption processes that encrypt data while in transit and at rest are essential to safeguard your valuable information from hackers and data leaks.
Encrypted Data at Rest
A growing number of governing bodies require organizations to encrypt their stored data to meet compliance demands. HIPAA, PCI, and FedRamp are three examples.
Azure users can rely on the Azure Key Vault to easily and quickly meet the data storage account criteria of strict regulating bodies. It is a secure repository that uses encryption at rest and secure access controls to store sensitive data safely.
Network Security
Keeping your network’s perimeter safe from malicious actors and zero-day vulnerabilities must be a priority for any business with an Azure environment. Azure Marketplace offers several reliable and robust network security services and tools organizations of all sizes need to add extra layers of protection to their network.
Some examples of these products include:
- Firewalls
- Botnet filters
- Antivirus solutions
- Web filters
Azure Networking Best Practices for Security
When securing the network side of your Azure landscape, you should adopt a Security Information and Event Management (SIEM) solution suited for your landscape. Any SIEM you assume should prioritize visibility, automate key security processes and involve a disaster recovery protocol.
Maintain Visibility
Continuous monitoring of your landscape increases your threat detection abilities, enables quicker incident response times and identifies vulnerabilities more efficiently. Several options exist to monitor an Azure cloud service or landscape. However, we recommend ones vetted and approved by Azure, such as Azure Monitor or a customized solution from a proven Azure partner.
Automating Security Scans
Azure provides continuous integration and continuous delivery (CI/CD) pipelines to automate the deployment and management of applications and Azure services. These pipelines can also automate security scans within your Microsoft Azure security infrastructure to help identify and remediate security vulnerabilities.
[sc name=”cta_blog” cta_title=”Are You One Hack from Losing Everything?” text=”Don’t Fall Victim to Ransomware. Secure Your Azure System Today.” button_text=”Find Out More” url=”https://www.atmosera.com/security-and-compliance/azure-data-protection-services/”][/sc]
By automating security scans, you can ensure that your code and infrastructure are scanned regularly for security vulnerabilities and that any vulnerabilities are remediated promptly.
Staying Up-to-Date
Azure is a constantly evolving platform, with new features and security fixes being released regularly. To ensure the security of your Azure deployments, it is crucial to stay up-to-date with the latest security fixes and features and regularly update your network and services.
Disaster Recovery Plans
No matter how much effort you put into securing your Azure landscape, developing a disaster recovery plan is essential in case the worst happens and there is a data breach or other security issue. A good disaster recovery plan should define roles and responsibilities within the organization for responding to a security incident and outline the steps for each action item.

Azure users who integrate Azure Backup and Azure Site Recovery into their disaster recovery plan minimize downtime during an outage. The services can easily recover and restore data quickly in case of a security incident.
Education Is Key to Microsoft Azure Security Best Practices
Educating your team on cloud-security risks, Azure best practices and protocols is essential to protect your network and data. All employees must be aware of the security measures in place to protect sensitive data and how they can help protect the company’s assets.
Azure users should also consider user education and employee training on topics such as risk management and secure coding practices. This will help ensure all organization members understand best practices for secure coding and how to identify potential security risks.
Cloud Security Training Checklist
When developing a cloud security training program for your team and access users, be sure to include the following:
Educate Teams on the Cloud Security Journey
Cloud security requires different cybersecurity approaches and protocols that your team may lack experience with. Educating them on cloud technology and model foundations will help them to secure the Azure landscape better.
[sc name=”cta_blog” cta_title=”Protect Your Azure Cloud Environment” text=”Atmosera specializes in deploying and modernizing Azure environments, so we know better than most how to secure yours” button_text=”Find Out More” url=”https://www.atmosera.com/azure-security/”][/sc]
Topics to cover should include:
- Cloud-specific threats.
- The shared-responsibility model.
- Cultural changes surrounding the adoption of a cloud-based environment.
Explain Cloud Technology
Team members who understand the environment they’re working in can better keep it safe from harm. When educating your organization about cloud-based services, be sure to include the following:
- What is cloud technology?
- What is cloud security technology?
- Steps users need to keep to protect the cloud service.
Protect Your Azure Landscape with Atmosera
Atmosera, we are an experienced Azure managed service provider and consultant for Azure solutions. We understand the importance of protecting your digital assets without compromising the power and capabilities of Azure.
We can help you develop and maintain a comprehensive security strategy that meets compliance requirements while protecting your business from cyber threats. Contact us today to learn more about how we can secure your Azure landscape.