Adaptability is at the heart of the CTEM approach. For this reason, Gartner suggests that organizations using it are 3 times less likely to suffer a significant cyber attack. This is because CTEM focuses on keeping your cybersecurity measures resilient against emerging threats.
| “Cyber threats are changing as quickly as technology. That’s why all organizations need a security protocol that’s equally as adaptable… if not more.” – Jacob Saunders, EVP of Professional Services, Atmosera |
CTEM also strengthens your organization’s ability to withstand and rapidly recover from cyber incidents. This is because the process ensures that security gaps are promptly closed. As a result, the impact and likelihood of cyber incidents are reduced significantly.
However, before you can take full advantage of this system, you need to understand it. This article will explore what CTEM is, its benefits, and how to implement it.
What is CTEM (Continuous Threat Exposure Management)?
Continuous Threat Exposure Management (CTEM) is a cybersecurity framework introduced by Gartner in July 2022. This strategy significantly differs from traditional, reactive cybersecurity methods. Instead of responding to threats after they occur, CTEM proactively identifies and mitigates potential cybersecurity risks in an organization’s digital infrastructure.
CTEM is not a single tool or technology. It’s a comprehensive strategy that involves a cyclic process with 5 stages. You can use it to adapt quickly to new security risks, reduce the risk of significant incidents, and maintain a high level of trust with stakeholders.
What Are The Benefits of Implementing CTEM at Your Organization?
1. Proactive Security Posture
CTEM transforms your organization’s approach to cybersecurity from reactive to proactive. This change enables you to identify vulnerabilities and address them before they are exploited systematically. It also encourages you to continuously monitor your digital systems so you can stay on top of potential security issues.
2. Improved Threat Detection & Response
Implementing CTEM improves your organization’s threat detection capabilities. The cyclic process facilitates real-time alerts to potential threats, which allows quicker and more effective incident response. This system of rapid alerts and response helps minimize the possible damage a cyber threat could cause.
3. Better Alignment With Business Objectives
CTEM ensures that cybersecurity efforts align with your business operations. This strategic alignment means prioritizing the most critical threats and vulnerabilities that could impact your organization’s key assets.
4. Compliance & Regulatory Benefits
CTEM can help you meet compliance with relevant regulations and governance frameworks. This is because it provides comprehensive oversight of your practices, which supports your ability to create a well-documented security policy.
| How Else Can You Keep Your Azure Assets Secure? |
5. Reduced Attack Surface
CTEM’s persistent detection and remediation efforts significantly minimize your organization’s attack surface. This minimization makes it difficult for attackers to find and exploit system vulnerabilities.
6. Continuous Improvement
Adopting CTEM encourages a culture of continuous improvement in cybersecurity practices. This involves constant monitoring, evaluation, and enhancement of your organization’s security posture. Such a practice will help you adapt to new and evolving cyber threats.
The 5 Stages of CTEM
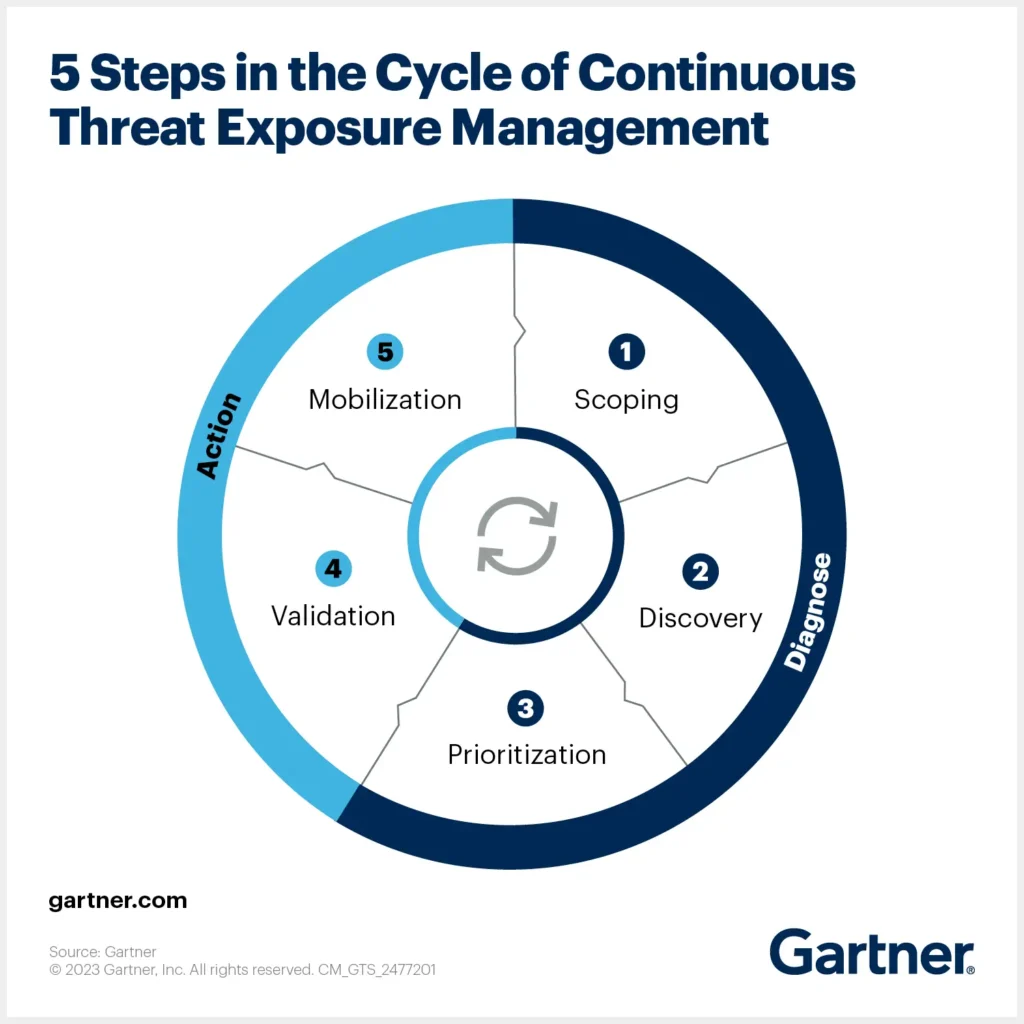
1. Scoping
In the scoping stage, you define which systems, assets, and stakeholders are involved. This stage involves a thorough risk assessment to determine which assets are most critical to your organization and therefore need urgent attention. This phase lays the foundation for the rest of your process.
2. Discovery
During the discovery phase, your team actively seeks out and identifies potential vulnerabilities within your organization’s systems and assets. This involves using various tools and techniques, such as penetration testing, to scan and assess for weaknesses.
3. Prioritization
Next, the vulnerabilities identified in the discovery stage are evaluated based on their priority. Vulnerability prioritization involves considering various factors like potential damage, the likelihood of successful exploitation, and how challenging it would be to address. The goal is to focus on the most critical vulnerabilities first.
4. Validation
The validation stage is about evaluating the effectiveness of your responses to the identified vulnerabilities. This includes testing the controls and processes that have been implemented to mitigate risks. It’s a good idea to include a range of experts in this process to ensure a comprehensive evaluation.
4. Mobilization
The final stage of the cycle is mobilization. The focus here is on implementing the controls and processes developed in the earlier stages. This involves mobilizing necessary personnel and resources and ensuring that all stakeholders are aware of their roles. Put simply, this phase is where the entire CTEM strategy is put into action.
CTEM vs. External Attack Surface Management (EASM)
External Attack Surface Management (EASM) is another proactive cybersecurity approach. However, its focus is specifically on identifying and managing an organization’s external digital footprint. The goal is to reveal internet-based risks that may come as a result of this footprint.
Here is a quick overview of the key differences between CTEM and EASM.
| CTEM | EASM | |
| Focus | Broadly focuses on continuously identifying, prioritizing, validating, and mitigating internal and external cybersecurity threats. | Specifically targets the identification and management of external, internet-facing assets and vulnerabilities. |
| Scope | Encompasses both internal and external digital assets. | Primarily concerned with assets and vulnerabilities that are visible and accessible from the internet. |
| Methodology | Involves a cyclic process of scoping, discovery, prioritization, validation, and mobilization to manage cybersecurity risks. | discovering external assets, evaluating their vulnerabilities, and managing these to mitigate potential external threats. |
| Approach | Based on a continuous process aiming to anticipate and mitigate risks before they are exploited. | Proactive in discovering and managing external threats, but may not cover internal issues. |
| Tools Used | Utilizes a range of tools for threat identification, risk management, and vulnerability management across all digital assets. | Employs tools specifically designed for scanning and monitoring the external attack surface, like internet-facing servers, websites, and online applications. |
| Business Alignment | Aligns with overall business objectives and cyber resilience strategies. | Focused on protecting the organization from external cyber threats. |
| Outcome | Enhances overall cybersecurity posture by continuously improving defenses. | Reduces the risk of external cyber attacks by managing and securing publicly accessible digital assets. |
Get Expert Advice on How to Use CTEM in Your Azure Environment
The CTEM approach can help any organization in any IT environment. The difference is in how you implement the 5-step cycle. Different systems have different functionalities, so naturally you will require different processes to execute CTEM effectively.
If you’re interested in bringing CTEM to your Azure system, Atmosera can help. Our team has over a decade of experience with Microsoft and is knowledgeable on up-to-date cybersecurity practices. Let us use this combined expertise to help you implement the best possible CTEM system for your Azure environment.

