3940
By: Byron Anderson
What is Defense in Depth?
Defense in Depth is a term commonly used in the security industry to note a security strategy that employs different layers of security instead of relying on only one or two elements. Historically security typically consisted of only perimeter security (a basic packet filtering firewall) and maybe a basic signature-based anti-virus solution. Fast forward to today and security threats have become much more advanced, requiring a much more comprehensive approach to security – and thus, Defense in Depth was born.
What does Defense in Depth look like?
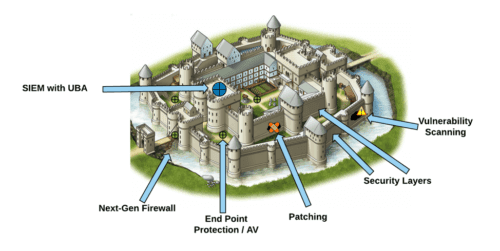
To explain this, we will use a Castle Analogy:
Imagine all of your valuable treasure (your data) is stored in a castle. Without any security elements a bad guy could simply walk up to your castle, sneak in the front door and take what was inside.
Now let’s add a Defense in Depth approach:
Next-Gen Firewall (Perimeter Defense)– This is a moat surrounding your castle with a single bridge across and a check point with guards. Anybody passing through the gate is inspected (think airport security) to make sure they are supposed to be passing through and don’t represent a threat.
Security Layers – This is a series of walls surrounding your castle with guarded checkpoints between each wall. To reach your castle, a bad guy would now need to bypass several checkpoints.
Patching (OS & Application) – This is a series of repair techs constantly repairing holes that form in your walls. This automatically fixes many of the holes that form in the wall over time so that bad guys can’t exploit those holes to breach your security layers.
OS: Operating System
Vulnerability Scanning – This is a series of inspectors constantly checking your wall for unrepaired holes where bad guys could get through. This allows you to see where there are holes in your wall and tells you how to fix them. Without it, you wouldn’t know where the holes are, nor where to focus and prioritize your available resources to fix those vulnerabilities.
End Point Protection / AV – This is a series of patrol guards looking for people doing bad things. If they see somebody exhibiting characteristics know to be harmful, they will isolate that person for further evaluation.
AV: Anti-Virus
SIEM with UBA – This is the head guard in a watch tower that can see what everybody is doing at all times, making sure nobody is trying to sneak about unseen. All of the other workers previously mentioned send constant reports to this guard allowing him to know everything that takes place. This allows the guard to see any bad guys that have managed to get into your castle (or that are trying to get in) as well as potential traitors (both intentional and unintentional) so that you can remove them from your castle if needed. This also gives you historical records of all observed activities.
SIEM: Security Information Event Management
UBA: User Behavior Analytics
Conclusion
As you can see, any single element does not provide a complete security solution. All of these different elements help provide safety nets in case one of the others fail. For example: if someone is able to sneak behind the wall, they may get caught by the Endpoint Protection/AV. Conversely, if the patching system fails to patch a hole in the wall, it will be identified by Vulnerability Scanning, and can then be quickly remediated.
