Using Kubernetes with Azure combines the power of Kubernetes container orchestration and the cloud capabilities of Azure. This combination supports complex deployment strategies and makes it easier for developers to deploy and manage applications. Still, Azure Kubernetes security policies are needed if you want to reap these benefits securely.
| “When integrating Kubernetes with Azure, security practices must consider the specific vulnerabilities associated with both the cloud and container environments. This requires some careful thought.” – Jacob Saunders, EVP of Professional Services, Atmosera |
Crafting these policies will largely depend on your organization’s needs and cloud strategy. However, there are some essential best practices that you should consider regardless of your unique requirements.
This article will show you 8 of those best practices. We’ll also discuss what Azure Kubernetes Service (AKS) is and how it works. Knowing this will help you be better prepared to implement your Kubernetes security policies based on recommended best practices.
What is Azure Kubernetes Service (AKS)?
Azure Kubernetes Service (AKS) is a managed container orchestration service provided by Microsoft. It simplifies the deployment, management, and operations of Kubernetes. Kubernetes is an open-source system for automating the deployment, scaling, and management of containerized applications.
How Does AKS Work?
AKS operates by abstracting and automating many of the complex processes involved in managing Kubernetes clusters. This way, you can leverage Kubernetes without the need to deal with the underlying infrastructure.
| What Are Kubernetes Clusters?: Kubernetes clusters are sets of nodes that operate using stateless protocols. Nodes run containerized applications. Every cluster operates with at least one worker node. Worker nodes host pods that contain the components of the application. Worker nodes and cluster pods are managed by the control plane. Clusters use multiple nodes to provide fault-tolerance and high availability. |
AKS automates the creation and management of Kubernetes clusters. It does this by leveraging the Azure infrastructure to provision virtual machines, set up networking, and configure storage options according to your specifications. It also continuously monitors the health of these clusters, automatically replacing unhealthy nodes to ensure high availability.
Deployment in AKS uses Kubernetes manifests or Helm charts, which describe your application’s structure, configurations, and requirements. When you submit these definitions to AKS, it interprets them and schedules the necessary containers to run on the cluster’s nodes.
AKS dynamically adjusts the number of running instances of your application using two key Kubernetes features: Horizontal Pod Autoscaler (HPA) and Cluster Autoscaler. HPA increases or decreases the number of pod replicas based on the current demand, while Cluster Autoscaler adjusts the number of nodes in the cluster itself.
Yet, the very features that make AKS efficient, like automated scaling and integration with Azure services, can also open up security vulnerabilities. However, you can avoid these potential vulnerabilities simply by following AKS security best practices.
| Learn More Azure Security Best Practices: |
8 Azure Kubernetes Best Practices For Security
1. Implement Secure Pod Access Controls
Pods are the smallest deployable units in Kubernetes that can run one or more related containers.
Limit pod access to resources by specifying security context settings in pods. Avoid running pods as the root user to minimize risk to node processes and services. This practice enhances secure container orchestration by ensuring that containers have only the access they need.
2. Use Role-Based Access Control (RBAC)
Leverage Kubernetes RBAC authorization and Microsoft Entra ID to manage access to Kubernetes resources. This setup ensures that only authenticated and authorized users can access your Kubernetes control plane and worker nodes.
3. Isolate Namespaces
Utilize Kubernetes namespaces to achieve logical isolation of resources, applying RBAC to enforce least privilege access. This approach helps in securing multi-tenant environments and efficiently managing permissions across different teams or applications within the same cluster.
Here’s a diagram that demonstrates how namespaces are organized in a Kubernetes network.
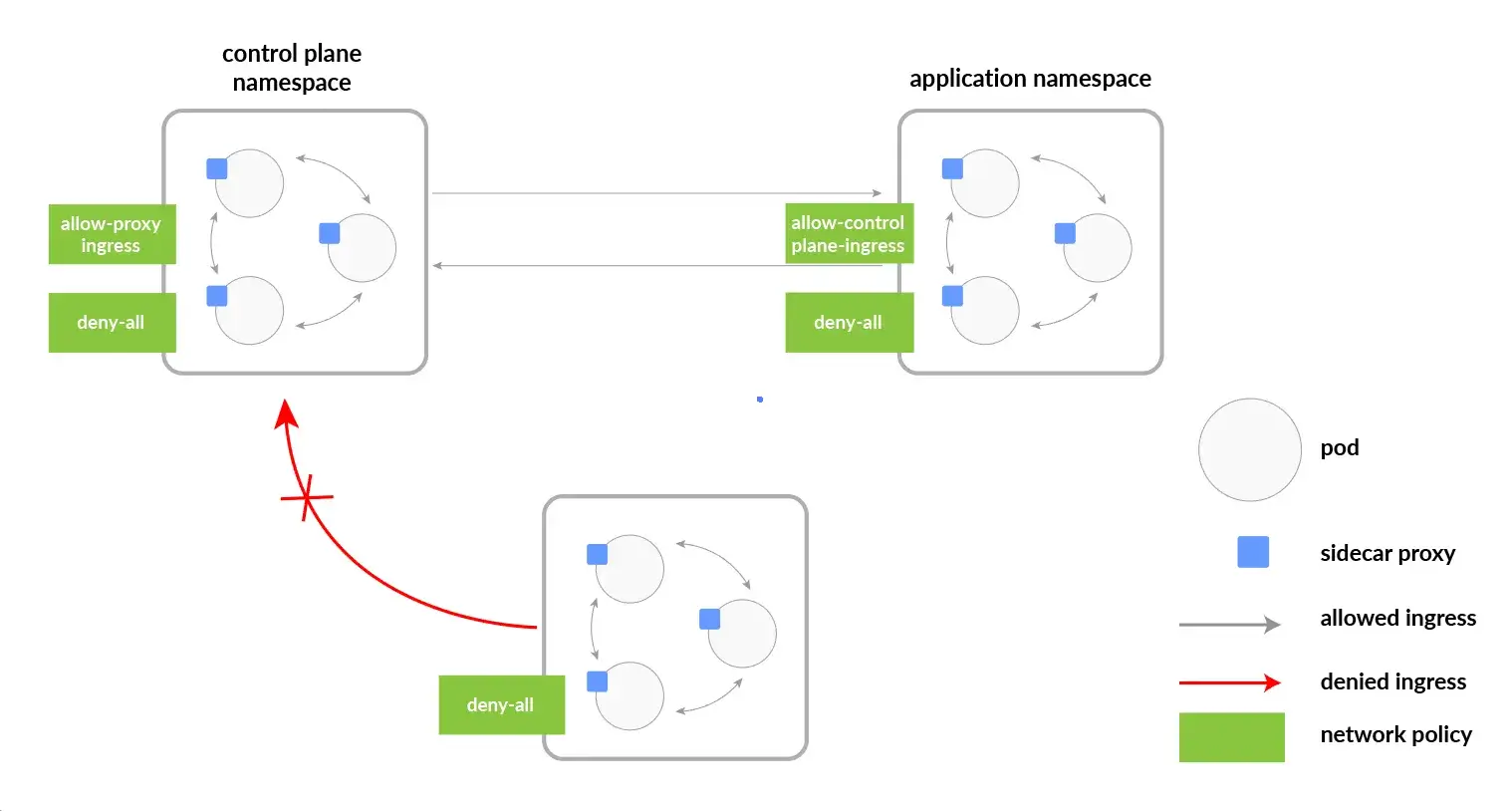
4. Deploy Secure Container Images
Regularly scan your container images for vulnerabilities using tools like Trivy or Clair and ensure that only secure, validated images are deployed to your AKS clusters. This includes using secure base images and updating them when security fixes are released.
5. Limit Exposed Credentials
Avoid hard-coding credentials in your application code. Instead, utilize Microsoft Entra Workload ID to securely access other Azure services without storing sensitive credentials in your application. Doing so reduces the risk of credentials being stolen or leaked.
6. Utilize Network Policies For Fine-Grained Control
Apply Kubernetes network policies to restrict the communication between pods within your AKS clusters. This helps to prevent unauthorized access and ensures that only allowed traffic can flow between pods, enhancing Kubernetes networking security.
7. Integrate Azure Key Vault For Kubernetes Secrets Management
Store sensitive information such as keys, tokens, and certificates in Azure Key Vault rather than embedding them in application code or container images. Use the Azure Key Vault provider for the Secrets Store CSI Driver to allow AKS pods to securely access this data.
8. Regularly Update Kubernetes & Nodes
Keep your AKS and its components, including all control plane components, up to date with the latest Kubernetes releases. This practice ensures you have the latest features and patches, which greatly reduces your security risks.
Protect & Enhance Your Kubernetes Environment With Expert Help
Using any Kubernetes version with your Azure services can seem overwhelming without experience or help. If you’d like to offload that burden, you can count on Atmosera’s managed security services to take care of your Kubernetes security for you.
We can also assist you with your broader Azure security needs beyond Kubernetes. This includes compliance monitoring, vulnerability scanning, managed Azure firewall services, and more.

