When it comes to securing your data in the cloud, Azure storage encryption is a critical component. Even more importantly it’s imperative to make sure your data remains secure at rest and in transit.
| “There is no question that cloud computing offers scalability and flexibility. As more businesses store and process sensitive data in the cloud, it’s critical to implement strong security measures to address potential risks.” – Jacob Saunders, EVP of Professional Services, Atmosera |
In this blog post, we will discuss the nuances of Azure storage encryption, as well as models; key types; and best practices for managing your encryption keys to keep your data secure.
Azure Backup Encryption: The Overview
Azure Backup makes sure that your data always stays protected by encrypting anything stored in the cloud. Using 256-bit AES encryption, one of the strongest encryption standards available, Azure secures your data at rest. Plus, this encryption is FIPS 140-2 compliant.
All data in transit is sent over HTTPS, keeping your data secure as it travels across Azure’s private network.
Microsoft Azure Encryption Models
Azure provides different encryption models, allowing you to decide how your data is secured and who manages the keys.
- Server-Side Encryption (SSE): Azure handles encryption directly. You have options for how your keys are managed:
- Service-Managed Keys: Azure takes care of everything.
- Customer-Managed Keys: You control the keys.
- Host Your Own Key (HYOK): If you need maximum control, you can manage your keys on your own controlled hardware.
- Client-Side Encryption: If you prefer to keep encryption entirely under your control, client-side encryption lets you encrypt data before it ever reaches Azure.
No matter the model you choose, Azure supports the flexibility to meet the security you need and maintain control over your data. For organizations that manage unstructured data, encryption is also a must for your Azure Blob Storage.
Elements of Azure Blob Encryption
Azure Blob Storage encryption keeps your data secure while at rest and on the move. A few of the elements that go into this include:
- Service-Side Encryption (SSE): With SSE, Azure handles encryption automatically. Your data is secured with 256-bit AES encryption. Plus, Azure encrypts your data as it’s stored and decrypts it once you access it.
- Client-Side Encryption: You also have the option to encrypt data yourself—before it ever gets to Azure. The client-side encryption model uses an envelope encryption system—one key is used to protect another.
- Encryption Scopes: You also have the tools to keep things organized. With encryption scope, you can apply unique keys to different containers or even individual blobs. This provides an added layer of security, especially for environments with multiple users or shared resources.
However you decide to manage your keys, Azure Blob encryption keeps your data secure.
Read More About Azure Optimization and Governance |
Understanding Azure’s Key Types for Encryption
To secure data in Azure, there are three types of keys you should be aware of:
- Master Encryption Key (MEK): This is your top-level key. With it, you lock down your Data Encryption Key (DEK) to ensure its protection. If you control your own keys, also known as “bring your own keys,” you can rotate the MEK for additional security.
- Data Encryption Key (DEK): This key encrypts your actual data and is stored on persistent media. The MEK provides an extra layer of protection for the DEK.
- Block Encryption Key (BEK): The key is generated from both the DEK and the specific data block. Your BEK is responsible for encrypting individual pieces of data—this means you can take an even more granular approach to security.
You have options to manage these keys, including letting Azure handle them with service-managed keys or you can take control with customer-managed keys through the Azure Key Vault (or your own hardware).
Key Management Options in Azure
Azure also gives you the option to choose how your encryption keys are managed—you decide how much control you want over securing your data.
- Platform-Managed Keys (PMKs): With this option, Azure takes care of everything. Your data is encrypted by default, and Azure manages the entire process.
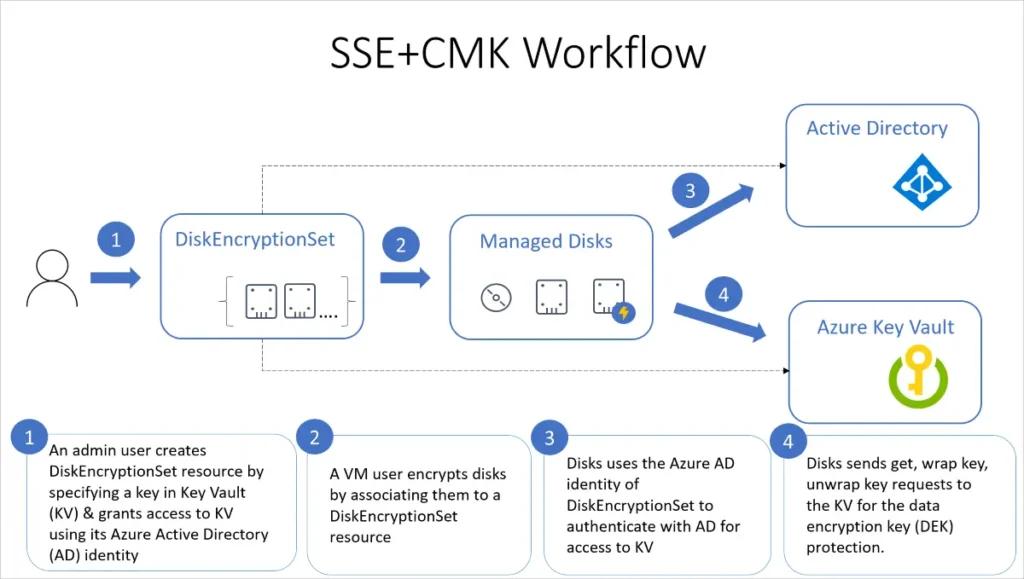
- Customer-Managed Keys (CMKs): CMKs offer a more direct form of control; with these, you take charge of your encryption. You can manage, rotate, and revoke keys as needed, which supports greater compliance and security. These keys can be stored in the Azure Key Vault or even in your own hardware security model (HSM). With Bring Your Own Key (BYOK), you can import your own keys directly into Azure.
- Key Encryption Key (KEK): KEKs encrypt your other encryption keys, creating a security barrier that protects sensitive cryptographic assets. This additional level of security helps your keys stay locked down.
Azure’s key management options let you keep your data secure in the way you prefer.
Best Practices for Managing Azure Encryption Keys
Managing your Azure encryption keys is a must for maintaining data security. Here’s how you can keep everything running smoothly.
1. Use the Azure Key Vault
For maximum control, store your keys in the Azure Key Vault—this uses FIPS 140-2 Level 2 and Level 3 HSMs to keep your keys protected. You can also create, import, and manage encryption keys in just minutes, all at the cloud scale. This means reduced latency and global redundancy. Plus, applications never have direct access to your keys.
2. Use Separate Vaults
Separate your vault by environment—development, staging, testing, production—to keep things where they should be. Isolate them by application to limit exposure if one area is compromised. This granular approach keeps your data and boundaries clear, limiting the potential damage of an attack. (Access to one vault does not expose others.)
3. Rotate and Log Keys
Regularly rotating your keys is a must. Set a rotation policy based on the way your organization works. This includes automatic renewals and expiry notifications through Event Grid. Frequent rotation minimizes risk and helps you keep unauthorized users out.
Secure Your Azure EnvironmentDon’t risk your data. Let Atmosera’s experts handle your encryption and cloud security. |
4. Backup Your Keys
Make sure you always backup your keys. Use the Azure portal to back up individual keys, secrets, and certificates. Store these backups in a secure location, and remember that you can only backup 500 past versions of each object.
While backing up your key vault, watch out for potential time-out errors and multi-version secrets and keep your service request limits within check to avoid throttling.
5. Avoid Hard-Coding Secrets in Code
Never embed secrets directly in your application or infrastructure code. Instead, use managed identities to keep access information secure and stored safely outside of your codebase. Ensure strict access controls and rotate secrets proactively to prevent misuse. Maintain an audit trail to track access and secure secrets against unauthorized exposure.
6. Enable Data Protection Features
Safeguard your Key Vault by turning on data protection features. Enable purge protection to prevent malicious or accidental deletion of secrets, even if soft-delete is already in place. This extra layer of security helps you make sure that your encryption keys and sensitive data remain intact and fully protected at all times.
Improve Azure Security and Operations
You don’t have to manage it all on your own. Atmosera offers professionally Managed Azure Security Services to help you optimize and secure your cloud resources. Whether you need advice on cloud governance, encryption best practices, or a fully managed approach, our experts are ready to support you.


